Vega is a GUID based open source tool used for testing the security of web applications. The tool can be used to test for disclosure of sensitive information, such as SQL injection, blind SQL injection, reflected cross Site scripting, stored cross site scripting, shell injections, and file inclusion vulnerabilities. A complete list of scanning modules can be viewed from the user interface.
Vega Installation
Vega is a Java tool that is compatible with Linux, Windows, and O SX. To install the tool in Linux, first run the update command to make sure that all the dependencies are installed and up to date.
apt-get update
After running the ‘update’ command, run the following Vega setup command. This installs the vega tool on the system.
apt-get install vega
If that does not work, try the installation with ‘sudo’ option.
sudo apt-get install vega
Using the Vega Tool
Vega GUI can be opened by typing ‘vega’ in the terminal.
vega
The target website can be added for scanning through ‘start new scan’ button or pressing the CTR+N command. This opens a window for entering the base url for scanning with an option to select the scope of scanning, known as Target Scope. The Target Scope allows selecting base paths and excluding urls or patterns of our choice.
After adding the target, move on to the next step to select the modules to be used for scanning. There are two types of modules available in the tool, namely Injection Modules and Response Processing Modules. The injection modules category contains a number of injection testing modules including SQL, BSQL, LFI, HTTP,XML, XSS, Blind OS, and Eval code injection.
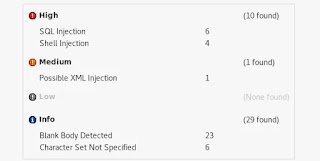
Similarly, the response processing category also contains a good list of modules to select. Some of these include: directory listing detection modules, insecure script checking modules, HTTP header checks, and cookie security modules. After configuring the scanning options, the tool starts the scanning of the target website based on the set parameters. Any vulnerability found is displayed by the tool as shown in the following screenshot.
What Bunny rating does it get?
Vega has a wide range of modules to test for web application vulnerabilities. Certain paths, files can be excluded from the scanning to make the process more targeted or specific. The tool also provides path to the vulnerable urls for further analysis. One of the major downsides is the false positive rate is pretty awful, this should be worked on to improve the tool and make it more of a viable option for pen tests, as a result we will be awarding this tool a rating of 3 out of 5 bunnies.



















No comments:
Post a Comment